I’m hoping to answer the most common questions burning in every IT professionals mind… How did we get here and why are previous solutions now considered insecure? We’ll start from the beginning, and if all goes well, we’ll finish up at the end…
I. In the beginning… Open and SKA
Open Wireless vs Shared Key Authentication. Long ago and far away, the 802.11 standards for wireless outline two forms of authentication- Open System Association (OSA) and Shared Key Authentication (SKA).
Open = no authentication
Shared Key = WEP
Open systems were just that- open, with no authentication. A free-for-all, come-join-the-network, nobody’s excluded kinda place.
With WEP, we configured 1-4 pre-shared keys that were used for all connecting wireless stations, and frequently used across APs in an organization. Again, we can see in the ‘Why WEP Sucks’ post why this is not ideal.
Recap- what’s wrong with WEP
There were many issues with WEP. Many of WEP’s issues are specific to it’s use in wireless applications. WEP would be an okay algorithm on wired medium, but we’ll see what it’s poorly suited for wireless. For a full review of why WEP sucks, read the post on WEP Sucks, so Why are You Using It?. Each of the bullets below are detailed in that post…
- Use of a streaming algorithm
- Per-packet master key re-use
- Group use of same PSK & Sharing of keys across APs
- Lack of authentication of network to client
- Confidentiality vulnerabilities with header
- Integrity vulnerability & replay attacks
- WEP Sucks, so Why are You Using It?
II. WPA and the Re-Engineering of WEP
The creation of the ‘i’. When the numerous WEP vulnerabilities were exposed, IEEE created the 802.11i group to increase security for wireless. WPA gave us the ‘Transitional Security Network’, the first step in the process towards developing ‘Robust Security Networks’.
Making the Most of Existing Hardware. One of the difficulties in re-engineering WEP was to create a more secure encryption process while still utilizing the current hardware. Implementations of WPA were a stage of transitional security, meant to address vulnerabilities in WEP while a stronger long-term solution was developed.
Wi-Fi Alliance, TKIP and WPA. The Wi-Fi alliance formed to create a security platform with interoperability between major vendors. (WPA came from ‘Wi-Fi Protected Access’). It wasn’t a standard, or even a framework, but an ad-hoc coalition of wireless vendors who had a joint goal of interoperability.
WPA Key Management & Authentication. WPA was a pre-standard subset of 802.11i, using both the specified key management and authentication architecture (802.1X) specified in 11i. Since the current hardware wouldn’t support AES (specified in 802.11i), WPA specified TKIP (Temporal Key Integrity Protocol) instead.
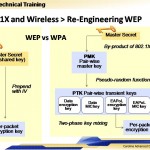
New WPA Key Creation. WPA uses the PMK to create PTKs (session keys). The key sets are created for each session (when a station associates with an AP). The PSF (pseudo-random function) to make the PTKs included nonces, counters MAC addresses, time and random numbers. Redesigning the key creation and usage help protect the master key by decreasing key exposure. See figure 1.
WPA’s Other Enhancements. Other features were enhanced in WPA to increase security, including:
- Increased the IV to 56 bits (increased secure keyspace by allowing 8 bits to exclude weak keys)
- Uses PTKs, which are generated for each session (again, increasing effective keyspace)
- Specifies IV rotation (to prevent key re-use)
- Uses MICHAEL for integrity (a non-linear algorithm)
- Authentication of network through 802.1X
- Addition of a sequence number (to protect against replay attacks)
- Protection of header and payload in integrity check (to protect against redirection attacks)
III. 802.11i- WPA2, the Sequel
WPA2/802.11i. Don’t worry- they’re the same thing. The IEEE 802.11i standard is the same as the WPA2. Finally we ended up with more capable hardware and encryption and reached the IEEE’s ideal ‘Robust Security Network’, using AES encryption with WPA2.
Current Wireless Security. Current 802.11i/WPA2 security is very similar to the pre-standard WPA, with a few differences. At the end of the proposed 802.11i transition, AES encryption was put to use as hardware was upgraded to allow for the change.
Two Biggest Changes from WPA to WPA2.
- Transition to AES
At the end of the proposed 802.11i transition, AES encryption was put to use as hardware was upgraded to allow for the change. - Enhanced Integrity Check
Leverages AES for AES-based CCMP
Key Exchange in 802.11i. The 802.11i standard leverages 802.1X for secure key establishment and authentication.
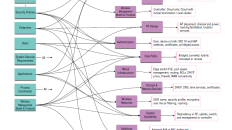
802.1X in 802.11i. EAPoL is easily adapted for use in wireless (in addition to native wired). *One important difference in 802.1X that’s different from previous authentication methods, is that the authentication is happening between the station and the RADIUS server (not the AP). Since the AP wasn’t involved in the key generation, the session key (from PTK) and the per-packet keys need to be shared also with the AP. The keys are secure transmitted after the TLS tunnel has been created and are passed along with the RADIUS access-accept message.
In this representation, different types of communication are colour-coded. EAPoL communication is show in black, while EAP conversations are shown in blue. RADIUs is shown in green and the TLS tunneling is shown in orange. With the colour-coding, you can clearly see the conversations between the station and the access point are EAPoL/EAP, while the access point talks to in RADIUS packets to the authentication server. See Figure 2.

TLS Tunnel from RADIUS. 802.11i leverages 802.1X for secure key establishment as well as authentication. The RADIUS server authenticates itself to the client, and vice versa. The tunnel created from the RADIUS server to the station allows secure communication and exchange of keys during authentication.
And so, here we are…
There are issues, concerns and considerations with 802.1X, but it is widely accepted as the most secure wireless authentication currently available. It’s secure key exchange, key rotation, master key protection and AES encryption are all best-of-breed in security technologies… for now.
# # #







[…] for you… For the full scoop, check out "A Brief History of Wireless Security" at Security Uncorked A Brief History of Wireless Security KNOWING YOUR NEED It really depends on the data you need to protect. In the US, we have specific […]
[…] seems a good read: Security Uncorked A Brief History of Wireless Security […]
[…] the history buffs, there is a A Brief History of Wireless Security from SecurityUncorked.com. CSOonline, back in May 2008, also published a very informative article […]
[…] public links >> wpa A Brief History of Wireless Security Saved by milestails on Thu 09-10-2008 WPAs Produce Year Round Saved by PaulTelner on Fri […]