There could be an entire book just on network segmentation; it’s a complex topic, with numerous options for achieving the mission, multiple places the policies can be configured, and multiple places those policies can be enforced. And yes, especially with newer zero trust models, the decision point and enforcement point for access may not be the same.
In the book "Wireless Security Architecture" I walk through the decision-making process of when to use what, how, and where when it comes to segmentation. Not only do we factor this into the design of wireless networks, but we also consider it in hardening the infrastructure as covered in Chapter 6, “Hardening the Wireless Infrastructure.”
This deep dive will explain filtering and segmentation as a concept, explore a few ways to enforce segmentation, and become familiar with the relationship of those options to our wireless architecture.
For a high-level overview, read "Wireless Segmentation Concepts: When, Why, and How."
The Role of ACLs and VLANs in Segmentation
When we talk about segmentation, we’re just describing any method (or combination of methods) to contain or separate certain devices (or data) from others on the network. Layer 2 segmentation uses VLANs which typically still require a layer 3 control. Layer 3 segmentation uses access control lists (ACLs) or other IP-based segmentation (such as Virtual Routing and Forwarding, or VRFs, described shortly). Filtering at layers above 3 happens at the port and protocol level up through the application layer and can be applied in several ways, including through ACLs and other policy enforcement options both wired and wireless.
ACLs in their traditional implementation are a set of rules or policies that dictate what traffic is allowed where, at layers 3 and higher. ACLs are most commonly associated with routers or routing switches, but as you’ll see, we have several options for applying ACLs including within the wired or wireless infrastructure, and on firewalls. Note that Cisco, Juniper, and other vendors have proprietary access control list features that operate at layer 2 or even the port level.
Filtering Traffic within Wireless and Wired Infrastructures
Before we delve into methods for filtering and segmenting traffic, the first big distinction to make is that, with wireless technology, there are times when we need to filter traffic within the wireless infrastructure (at the AP, controller, or gateway), and times when we need to filter traffic once it’s on the wired network, after egressing the wireless infrastructure. Obviously, the wired infrastructure can’t filter traffic over the air, and (in most cases) the wireless infrastructure can’t filter traffic once it’s left the wireless and is passing through the wired network.I say “in most cases” because there are some vendor-specific implementations that are bordering on this.
Filtering Within the Wireless
Let’s first examine some ways we may enforce segmentation within the wireless infrastructure—that is, enforcing access rules within the APs and/or controller versus within the wired network.
The figure below compares segmentation on the wireless infrastructure versus the wired infrastructure. On the left, the wireless infrastructure is able to segment traffic between endpoint devices, such as not allowing the laptop to communicate directly to the smartphone, or the phone to the LAN. On the right, wired segmentation is applied and in this example traffic from the smartphone is also not allowed to the LAN, but that’s enforced on the wired network, not at the AP or controller.
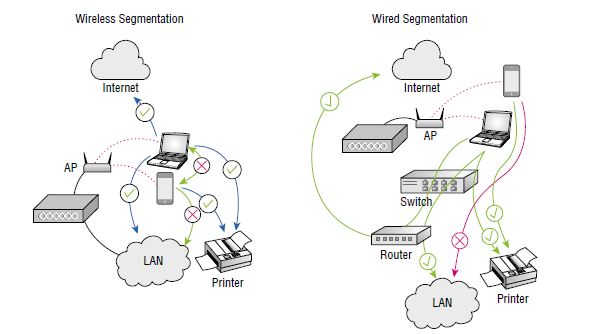
The trick to proper segmentation is to know where along the data path the traffic filtering needs to be enforced, with the understanding filtering may need to be applied in more than one place. In an SSID where the client data is bridged from the AP to the edge switch, there should be filtering not only within the wireless infrastructure, but also on the wired infrastructure since the traffic is dropped at the edge for forwarding and routing.
Conversely, in an SSID where the client data is tunneled from the AP to a controller, the filtering can be enforced fully within the wireless infrastructure, in most cases eliminating the need to manage ACLs on routers within the wired infrastructure.
Filtering with Inter-Station Blocking on Wireless
One of the most basic controls we have within the wireless infrastructure is the use of inter-station blocking. Inter-station blocking simply prevents Wi-Fi clients on the same network or SSID from communicating with one another. It was a standard operation in Wi-Fi deployments for many years, but more recently became a troublesome setting as more and more protocols use peer discovery for proper function.
I’m using the phrase “inter-station blocking” to avoid any confusion with other operations, but this feature may be referred to as peer-to-peer blocking in some vendors’ products or documentation. Peer-to-peer communications are also often referred to in terms of ad-hoc networking, which is different in that ad-hoc networks bypass the enterprise infrastructure completely.
Specifically, enabling inter-station blocking impacts various direct connection protocols such as those required for direct printing, screen casting, and other applications that require client-to-client connectivity over the Wi-Fi infrastructure. In my book “Wireless Security Architecture” Chapter 6, Hardening the Infrastructure, I dive further into the security ramifications of various peer-based client communications and the risks they pose. Spoiler alert — it’s one of the first ways pen testers and attackers gain entry to a network.
Filtering with SSIDs/VLANs on Wireless
The most commonly used and straightforward approach to segmenting traffic within the wireless infrastructure is to use SSIDs that place endpoints on different client VLANs. This can happen through static configuration of the SSID—for example, “ACME-IoT” SSID may place endpoints on VLAN 99, which is Internet-only, whereas the “ACME-Secure” SSID may place endpoints on a production VLAN 20.
There are also options for a dynamic VLAN assignment. The most common implementation of this would be on the Enterprise/802.1X secured SSIDs where we simply instruct the authentication server to attach a standard RADIUS attribute along with the authentication approval. When the wireless infrastructure gets the “OK” from the RADIUS server, it would be accompanied with an instruction for the specific VLAN, which may be based on one or more user or device attributes.
Filtering with ACLs on Wireless
There are also options to filter traffic within the wireless infrastructure at a more granular level than VLANs. Although I’m referring to this section using “ACLs,” this feature may come in many forms, including access control policies that look like router ACLs, or policies that mimic firewall rules. The point here is to demonstrate the ways of controlling traffic within the wireless infrastructure above layer 2, using layer 3 and higher methods such as specifying traffic based on IP address, subnet, port/protocol, or even application signatures. With these controls in place, traffic is being filtered by the wireless infrastructure, but within the wired components, not over the air, which is always layer 2.
Similarly to how we specify rules in firewalls, the wireless vendors often have options to define labels or tags used like address objects, which allow you to specify policies using names instead of IP addresses. For example, in some platforms you can specify any traffic coming from a portal SSID as “guest” and apply rules to that guest traffic without ever referring to a subnet like 192.168.99.0/24. You could also create a label of “conference room printer” and specify the IP address (or hostname), such as 10.10.20.186 (or conf01print.acme. com) and then apply a policy to allow “guest” to “conference room printer.” In many cases, you could even be more granular and only allow certain ports or protocols in that policy. Labels are a great way to simplify otherwise complex ACLs and reduce the potential for human error.
Wireless vendors often refer to their ACL-based filtering using their own terms, such as defining “roles” with Aruba Networks or “policies” using VXLAN in Juniper Mist. In addition to their self-defined names of features, vendors also offer some proprietary secret sauce to help make specifying and applying segmentation easier to manage.
Lastly, it’s worth mentioning that we can also send dynamic or downloadable ACLs via RADIUS attributes, like the method described previously with dynamic VLANs.
Filtering Within Wired Network
That covers all the common segmentation methods implemented within the wireless infrastructure (at the AP or controller/gateway). Next, we’ll look at the options for segmenting or filtering traffic within the wired infrastructure.
Filtering with VLANs on Switches
Controlling traffic with VLANs is a blend of layer 2 and layer 3 enforcement. While VLANs are, by IEEE definition a layer 2 standard, they are most often attached to an IP-based interface, which means we must then implement layer 3 controls.
Before we get into ACLs, let’s cover those rare occasions when there can be pure VLAN-based segmentation. If we were to configure VLAN 20 throughout our infrastructure and not assign any IP addresses to the VLANs nor IP-based routing interfaces for VLAN 20 anywhere in the routing switches, then we will have successfully implemented layer 2 segmentation, and that VLAN’s traffic will not be forwarded or routed to or from other VLANs. In practice, however, there will almost always be a need to route the traffic somewhere—if nowhere internally, something in that VLAN is sure to require Internet access.
Filtering with ACLs on Routing Devices
Most times we’re not able to do pure layer 2 segmentation and we’re going to rely on layer 3 ACLs somewhere. In cases where traffic is egressing the wireless network and is then routed on the wired side, there will be a need for ACLs on wired routing devices.
Most commonly, this need arises when wireless client traffic is bridged at the edge switch. At that point the client traffic has left the wireless infrastructure and is being forwarded or routed just like the rest of the wired traffic on the network. In this architecture, the wireless client is frequently served a DHCP assignment from a scope specifying a gateway and DNS on the wired network, and as such that gateway routing device should have appropriate ACLs to control traffic to and from that client data subnet.
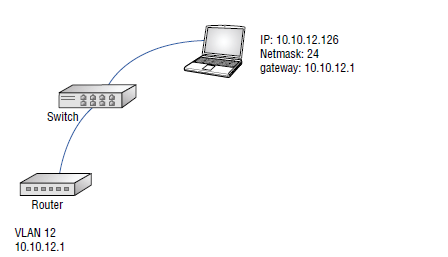
The figure below shows an endpoint with an IP address 10.10.12.126 and a 24-bit subnet mask. Its default gateway is 10.10.12.1, which is an IP address of the routing switch also depicted in the figure. This image tells us two things. First, for traffic not already filtered at the AP, any ACLs will need to be applied at the routing switch. Second, if this is a wireless client, we can infer that the traffic is bridged, not tunneled.
Filtering with Policies on Firewalls
In this architecture, the firewall is where the traffic filtering happens and can be specified at a level of granularity not supported in all routing switches. In addition to granularity, firewalls can offer ease of management as most firewall policies can be name-based with address objects by IP or subnet, making it easier to specify a policy such as “allow guest to Internet,” “deny guest to LAN interface,” or “allow guest to conference room printer.” One advantage with firewalls is the visibility from logging. It’s possible to log allowed or denied traffic and offload that easily to tools to assist with forensics in incident response.
Using firewalls for traffic filtering is most common for subsets of traffic, users, or devices. For example, it frequently makes sense to direct all guest Internet-only traffic out directly through a firewall instead of routing it internally. It may also make sense to protect resources or subnets with sensitive data and applications behind a firewall and only allow specific traffic to and from them.
Filtering with Network Virtualization Overlay
The final method of traffic segmentation comes in the form of vendor-specific implementations of network virtualization overlay technologies such as Virtual Routing and Forwarding (VRF) and Ethernet VPN-Virtual Extensible LAN (EVPN-VXLAN).
VRF, VXLAN, and other virtualization technologies are supported by most enterprise network vendors including Juniper, Cisco, and HPE Aruba, among others, but may have vendor-specific implementations that don’t allow integration across platforms.
VRF is most simply described as a layer 3 version of VLANs. It’s a protocol used by routing devices that allows virtualized routing tables. Originally a carrier technology, it’s been commonly used in LANs for years (usually as VRF lite) to segment traffic more deterministically without having to manage complex ACLs.
EVPN-VXLAN is a datacenter technology that is making its way toward the network edge. It extends layer 2 connectivity as a virtualized network overlay across an existing layer 3 physical network. Put more simply, it lets us extend VLANs across routed boundaries and keep the layer 2 properties.
That wraps up today’s deep dive on wireless segmentation and filtering! If you found this helpful, please check out my newest book “Wireless Security Architecture” published with Wiley.
 | This post includes excerpts from Chapter 2 of WIRELESS SECURITY ARCHITECTURE. JOHN WILEY & SONS. More on network segmentation can be found in Chapter 2’s section titled “Understanding Data Paths” and Chapter 6 on “Hardening the Wireless Infrastructure”. |
Feature photo of diver by Jeremy Bishop on Unsplash