In upcoming guides I’ll be sharing details on WPA2 versus WPA3, best practices for migrating on each network type, and other recommendations for WiFi security. This post provides non-WiFi-pros a common baseline for future learning.
I'll go ahead and say this - for many of my readers, there's maybe just one interesting tidbit here for you. This post is outlining the three types of WiFi networks from the perspective of SSID security profiles.
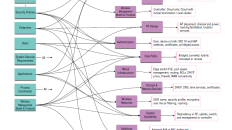
The 3 Types of SSID Security Profiles
- Open
- Personal (uses a passphrase, formerly known as a PSK)
- Enterprise (uses 802.1X with EAP)
The designations of “Personal” and “Enterprise” and even “Open” can be a bit misleading and may not mean what you think they do. These terms have very specific meaning from the Wi-Fi Alliance and in fact are copyright to that organization.
Here's some interesting trivial on naming conventions. In enterprise-grade WiFi products, manufacturers may represent the networks and capabilities differently in the configuration screens. For example, one vendor may show "WPA3-Enterprise" and another may represent the same option as "WPA3-EAP" or "WPA3-802.1X". The labels of "Open", "Personal", and "Enterprise" in WiFi security are specific to the Wi-Fi Alliance and manufacturers must have completed the appropriate Wi-Fi Alliance certification in order to use those designations in the product.

Consumer and residential WiFi routers such as those provided by your Internet Service Provider will only support Open and Personal networks. With the advent of cloud-hosted RADIUS servers that can make deploying Enterprise class networks a breeze, I do hope the industry will start supporting Enterprise/802.1X in residential routers, but for as much as I’m an optimist, the realist in me knows that’s highly unlikely in the near future.
What's an SSID ? If you're new to networking or not a networking professional, the SSID is simply the WiFi network name. If you see "Starbucks Guest" or "Hilton Honors" those are the names of the WiFi network SSIDs. There are additional technical nuances between SSIDs, ESSIDs, BSSIDs, and the backend configuration of complex systems, but none of that is relevant for today's content.
Open Networks
The most common examples of Open networks are those SSIDs that serve captive portals and SSIDs that require no interaction to join the network. Captive portals of course are common in coffee shops, hotels, and many airports. In a captive portal mode, the endpoint is allowed to join the Open network, but the user is then prompted to interact with a portal in a web browser to gain Internet (or other network) access. The web portal may simply ask the user to agree to terms of use, or it may authenticate or register the user. Hotels that ask you to enter your last name and room number are an example of the latter. In an Open network without a captive portal, the user simply clicks the network name and no further action is required. Examples may be found on Disney properties and in many hospital guest networks.
Open networks:
- Don’t require the device/user to authenticate to the WiFi network to associate/connect to the AP
- May include a captive portal to gain an additional level of network or Internet access
- May not have a captive portal, in which case the only action required is to select the network from the list and connect
- Traditionally were not encrypted but newer Enhanced Open networks will offer this
Open Networks and Encryption
Until very recently, Open networks have not have a way to support encryption of traffic over-the-air between the AP and the endpoint. Traffic is usually encrypted other places (such as from user browser to service application) but that’s not guaranteed. Released around the time of the new WPA3 security enhancements was Enhanced Open, which adds unauthenticated encryption to the Open network. As of July 2022, Enhanced Open networks are still not as widely supported by endpoints as we might like, and the experience to configure the back end is a bit mucky and varied. Stay tuned though, because Enhanced Open offers promising reward!
Words and phrases associated with an Open network include open, enhanced open, owe, captive portal.
Learn more about Enhanced Open in WiFi Security: WPA2 vs. WPA3.
Personal Networks
Personal networks are the classification of networks that require the user or device to use a passphrase when connecting to an SSID. With very few quirky exceptions, the passphrase is validated within the WiFi infrastructure (by the AP or controller) and requires no additional backend infrastructure such as a RADIUS server.
Personal networks:
- Use a passphrase to connect to the network
- Add the benefit of encryption over traditional Open networks
- May include vendor-specific implementations of multiple or individual/personal device keys (MPSK, PPSK)
- Operate very differently between WiFi security protocol versions WPA2 (very vulnerable to attack) and newer WPA3 (much more secure)
- Are currently used readily in business and enterprise networks, especially for IoT, headless devices, and even biomedical and voice communications
- Are sometimes used as a guest network to add encryption and some control over who’s joining the network
Personal Networks in the Enterprise
“Personal” can be a bit of a misnomer since these networks are extremely prevalent in enterprise networks. There are myriad devices that don’t support 802.1X and therefore organizations (including most business offices, hospitals, manufacturing facilities, etc.) will have one or more networks to support Personal/passphrase connected devices.
Perhaps even more surprising, use of Personal/passphrase networks has been recommended to address issues with roaming and key exchanges associated with a poorly-designed secure 802.1X network. In fact, NIST guidance for critical endpoints such as biomedical devices specifies Personal/passphrase connections because availability trumps security for many healthcare use cases. Similarly, vendors that support push-to-talk and real time voice communication also often recommend Personal/passphrase networks for those endpoints to avoid latency when roaming across a poorly configured secure 802.1X network.
The Evolution of Personal Network Security
As we rounded the corner and entered 2022, most network and security professionals were in sync in the message that “Personal/passphrase networks aren’t secure.” And while that was true, as we roll out the new WPA3 security suite, that tune has changed drastically.
WPA2-Personal networks that use pre-shared keys are absolutely not secure. They’re susceptible to a host of malicious attacks I’ll cover in an upcoming post. For now, know that WPA3-Personal works very differently than WPA2-Personal and will be considered a viable and secure option even for many corporate assets.
Words and phrases associated with Personal SSID networks include personal, passphrase, pre-shared key, PSK, and SAE along with WPA2-Personal, WPA3-Personal, WPA2-PSK, and WPA3-SAE.
Enterprise 802.1X Networks
The gold standard in WLAN security for over a decade, Enterprise class networks use IEEE 802.1X along with EAP (Extensible Authentication Protocol) for authentication of the endpoint and/or user to the network. The IEEE 802.1X standard defines the opening and closing of the port (in the case of WiFi that’s a virtual/logical port), and EAP is an IETF RFC that specifies a framework for authentication options.
Again here, “Enterprise” can be confusing since one may consider any SSID in an organization/business is an “enterprise network” but remember these are specific Wi-Fi Alliance terms, not common language.
Enterprise SSIDs use 802.1X and EAP to authenticate the endpoint/user through certificates, username and password credentials, tokens, or combinations of those. Most products will require a RADIUS server be configured to support these connections and assign policies. Within 802.1X-secured networks, there are many additional settings and options including the authentication mechanism, the secure tunnel the credentials are sent through, policies, timeouts, and more.
Enterprise/802.1X networks:
- Are the current gold standard for WiFi security, if implemented properly
- Authenticate endpoints and/or users by certificates, username/password credentials, tokens or a combination of the three
- Should always authenticate the server to the endpoint via a certificate
- Require a RADIUS server and a directory of user/device accounts
- Allow for authentication bypass for endpoints that don’t support 802.1X

MAC Authentication Bypass with 802.1X
The 802.1X standard supports a “bypass” mode to allow endpoints that can’t participate in 802.1X to authenticate using their MAC address. As a security professional, I’ll caution that use of a MAC address is not considered authentication; it’s an assertion of identity, not proof of identity since MAC addresses are not immutable and can be very easily spoofed.
In a future post, I'll cover specific recommendations on handling MAB securely in Enterprise networks, which entails separating them on different SSIDs.
Words and phrases associated with Enterprise SSID networks include Enterprise, 802.1X, EAP, RADIUS, certificates, WPA2-Enterprise, and WPA3-Enterprise.
If you don’t live in the world of WiFi, I hope this offered a good intro and overview into the three types of WiFi security options in SSID profiles. Upcoming posts in this series will build on this knowledge and terminology. Stay tuned!
You can find more details about WiFi security, WiFi security protocols, WPA2 and WPA3 in my latest book "Wireless Security Architecture: Designing and Maintaining Secure Wireless for Enterprise."










[…] For more on the three classes of WiFi security, read WiFi Security: The 3 Types of WiFi Networks […]
[…] you need to understand the differences between a Personal, Enterprise and Open network. In “WiFi Security: The 3 Types of WiFi Networks”, Jennifer Minella, a network security veteran and Tech Field Day delegate shines light on the […]