There’s a new Sheriff in the Town of WiFi Security, and its name is WPA3. The WPA3 (Wi-Fi Protected Access version 3) is the latest WiFi security suite program from the Wi-Fi Alliance. Most networks today are using WPA2 — a standard ratified in 2004 and required in products starting in 2006. Yes, that means we’ve been using the same WiFi security suite for ahem over 15 years! Eeeeekkkk
WPA3 covers the security suite used in Wi-Fi Alliance designated Personal (passphrase) and Enterprise (802.1X) WiFi networks. Although not technically part of the WPA3 suite, the release of Enhanced Open for adding encryption and integrity to Open networks coincides loosely with WPA3.
For more on the three classes of WiFi security, read WiFi Security: The 3 Types of WiFi Networks
In the agile world of tech, it’s almost ridiculous how long this has taken. Certification for WPA3 by the Wi-Fi Alliance began in June of 2018, but four years later we’re just starting to see adoption.
I hope this series on WiFi security and WPA3 will spark readers into action, and provide an easy-to-follow framework for moving from legacy WPA2 to the latest WPA3 hotness. Stay tuned for a full detailed guide to planning your migration. Before we get to the migration plan, let’s cover the major enhancements of WPA3.
This post includes:
- WPA3 Security Enhancements (including 6 sub-sections)
- Finding Security Settings in WiFi Products
- Following Along with WPA3 Enhancements
- Summary
WPA3 is covered in much more depth in my book "Wireless Security Architecture" starting with Chapter 2 "Understanding Technical Elements" section on "Understanding Security Profiles for SSIDs".
WPA3 Security Enhancements
WPA3 replaces its predecessor, WPA2, and adds several significant security enhancements including:
- Required use of Protected Management Frames (PMF) to add integrity and support availability
- Protection from downgrade attacks
- Disallowance of legacy and deprecated protocols
- Enhancements for Enterprise/802.1X secured networks
- Enhancements for Personal/passphrase-based networks
- Enhancements for Open networks (not technically part of WPA3 but its close cousin)
I’m going to dive more into each of these bullets in the following sections.
1. Required use of Protected Management Frames (PMF)
In the description of PMF, the Alliance focuses on the benefit of bringing “integrity” to the management traffic. This manifests two ways. First through mutual authentication of the endpoints to the AP, and secondly through encryption of select management traffic. Both features are delivered through cryptographic functions.
The mutual authentication ensures management traffic can’t be spoofed from the AP or the endpoint, and protects endpoints and users from malicious attacks that start with a forced dis-association or de-authentication through a spoofed packet. With PMF, the AP keeps the equivalent of a session table for each endpoint, and any requests to modify session state are authenticated and validated against the list.
By ensuring the communications between the AP and client are authentic, authenticated, and (at times) encrypted, PMF enables security protections in several important ways.
Security Enhancements with PMF
- Protection from client spoofing
- Protection from AP spoofing
- Protection from some denial-of-service attacks
- Protection from replay attacks
- Protection from some on-path (AKA man-in-the-middle) attacks
Although there have been legitimate uses of spoofing management frames (such as using de-authentication messages to keep managed corporate devices from connecting to rogue APs), ultimately the industry has realized the benefits of securing the management traffic outweigh the few lingering use cases for keeping it unprotected. With PMF enabled, neither clients nor an AP will be able to send management packets as another entity, regardless of whether it’s a legitimate use case or malicious attack.
A Sidebar on PMF vs. MFP Let’s take a stroll down to the netherworld of acronyms. The 802.11w standard is referenced by the Wi-Fi Alliance as Protected Management Frames (PMF) and referenced in the IEEE specification as Management Frame Protection (MFP). Those are both the same thing (802.11w) but should not be confused with Cisco’s vendor-specific feature suite also called Infrastructure Management Frame Protection (MFP), which is a collection of controls for infrastructure integrity.
2. Protection from downgrade attacks
I’m presenting this bullet with a bit of a caveat. As it stands now, WPA3 incorporates controls to prevent downgrade attacks. It’s an especially impactful feature when you consider that many attacks start by forcing an endpoint to a lower security suite, and/or a deprecated protocol and then attacking through a known vulnerability.
In full WPA3-only networks (versus Transition Mode networks that support WPA2 and WPA3) the new security suite will protect endpoints from using outdated and weak ciphers and protocols.
In Transition Mode networks, the original plan was to prevent a WPA3-authenticated endpoint from accidentally or maliciously being forced to roam to a WPA2 network without the user’s knowledge. The caveat is that there may be less protection than originally planned in this scenario. My understanding is that many residential WiFi router vendors are pushing for endpoints to move seamlessly to lower-security networks in order to streamline their user experience and reduce support calls from consumers. If that happens, it will certainly impact this aspect of security for business networks. We’ll all stay tuned for updates on this front.
3. Disallowance of legacy and deprecated protocols
Across the board, the WPA3 security suite enforces stronger cryptography and disallows the use of deprecated and weak ciphers such as TKIP. Certainly, it’s one of the top benefits in moving from WPA2 to WPA3. The minimum 128 bit encryption applies to WPA3-Personal as well as WPA3-Enterprise.
4. Enhancements for Enterprise/802.1X secured networks
I’m hitting the highlights in WPA3-Enterprise features because the biggest WPA3 “bang” really comes in the WPA3-Personal network security.
For WPA3-Enterprise, the three biggest security boosts come from Protected Management Frames (PMF), the introduction of an optional 192-bit encryption mode, and the shift away from deprecated protocols like TKIP.
In addition to the required use of PMF ubiquitous with all WPA3 deployments, the WPA3-Enterprise’s main differentiators from legacy WPA2-Enterprise are:
- Addition of an optional 192-bit encryption mode for stronger authentication (for EAP-TLS only, primarily designed for security-conscious customers including government, defense, finance, and industrial)
- Required use of authentication (RADIUS) server certificate validation for certificate-based endpoint authentication (EAP-TLS)
- Stricter requirements for user override of server certificates
- Prohibition of less secure and deprecated encryption protocols (including TKIP)
- Addition of robust management frame protection through 802.11w PMF
Anytime we upgrade security protocols in WiFi, the change has to happen on both ends — in this case with the WiFi system, and the endpoint connected to it. Understanding that we don’t always have the luxury of flipping a switch and migrating every endpoint to the new security suite, there are modes to support both WPA2 and WPA3 concurrently on the same SSID. The Wi-Fi Alliance refers to these formally as Transition Modes.
WPA3-Enterprise can be configured on an SSID in one of three ways:
- WPA3-Enterprise Only mode (WPA3 only)
- WPA3-Enterprise Transition Mode (WPA2 and WPA3)
- WPA3-Enterprise 192-bit mode (WPA3, 192-bit only)
The minimum configuration for WPA3 supports 128-bit encryption, and the 192-bit option of course increases that cryptographic strength. The 192 is a merging of lengths of keys and hashes.
WPA3 Transition Mode and Migration Options
As you can tell by its name, the WPA3 Transition Mode will support WPA2 and WPA3 both on the same SSID. This brings the benefit of supporting a phased migration without having to add an SSID and update connection settings (to that new SSID) on the endpoints, but has the negative side effect of a false sense of security and certain continued vulnerability.
With Transition Mode networks, you’re only as secure as the weakest link, and allowing WPA2 endpoints means (under most conditions/configurations) your shiny new WPA3 Transition Mode network is dumbed down in large part to legacy WPA2 capabilities. The WPA3-capable endpoints are more protected (especially via PMF) but the remainder of the network remains at risk to spoofing and other attacks.
Having said that, if you must use a Transition Network, it’s better to do it on an Enterprise class network than a Personal class network, as you’ll see.
5. Enhancements for Personal/passphrase-based networks
By far, the biggest leap forward in WiFi security from WPA2 to WPA3 is seen on the Personal class of networks that use passphrases.
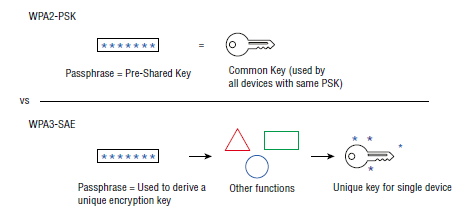
With WPA3-Personal the legacy WPA2-Personal Pre-Shared Key (PSK) mechanism was replaced by Simultaneous Authentication of Equals (SAE). With SAE comes some really impactful security enhancements, not the least of which is a separation of the encryption key from the passphrase. I’m a bullet-list kinda’ gal so let’s cover them each. WPA3-Personal includes these security enhancements:
- Use of Protected Management Frames (PMF), covered above
- Resistance to offline dictionary attacks
- Separation of cryptographic key derivation from the user-entered passphrase, which means we have strong cryptography even with a short passphrase
- Provisioning of unique cryptographic keys for each endpoint (even with the same passphrase)
- Perfect forward secrecy, which prevents an attacker from decrypting past packets even if the passphrase is compromised
Security with WPA2-PSK vs. WPA3-SAE
In the SAE authentication function, the user-entered passphrase is not directly related to the encryption keys, meaning even if an attacker has discovered the passphrase, she/he would not be able to decrypt other traffic. In addition, this means the user-entered passphrases can be shorter and less complex while still providing the same cryptographic strength. Of course, if the passphrase is too simple or short, it would be easy to guess and allow an attacker on the network, which is obviously undesirable for many reasons.
Another benefit of SAE is perfect forward secrecy, which is a cryptographic feature that protects traffic from being decrypted retroactively. If an attacker were to derive keys, it would not be possible to have captured earlier traffic and then decrypt it after the fact.
Let's Stop saying PSK! Most network professionals are familiar with the term "PSK" or "Pre-Shared Key" and for all of eternity, that's been used interchangeably with "passphrase" on WPA Personal networks. PSK is specific to WPA2-Personal, and that is replaced with the much more secure Simultaneous Authentication of Equals (SAE) in WPA3-Personal. So, when we're talking about entering that 'thing' let's call it the passphrase instead of the PSK.
The full migration guide will be available soon. In the meantime, there are two ways to get started with WPA3-Personal.
WPA3-Personal can be configured on an SSID in one of two ways:
- WPA3-Personal Only Mode (WPA3 only)
- WPA3-Personal Transition Mode (WPA2 and WPA3)
Migrating from WPA2-Personal to WPA3-Personal
If using Transition Mode, only use it for as long as you need to migrate the endpoints, and don’t use the same passphrases for WPA2 and WPA3 connected endpoints. I realize that sounds simple but can be rather complicated on many WiFi platforms.
SAE’s security is leaps and bounds better than that of its PSK predecessor; but for all the cryptographic genius it entails, it’s all for naught if you reuse WPA2 passphrases or choose short or easily guessed passphrases.
Ideally for WPA3-Personal network migrations, you’ll want to configure a new dedicated WPA3-Personal Only SSID, and move endpoints to it as you go. Remember that WPA3 is very often simply a software upgrade for endpoints, but they will need driver updates. Traditional platforms like Windows under corporate management will get regular updates, but the unmanaged endpoints, possibly non-domain-joined devices, and all the IoT-esque things may require a more hands-on approach.
6. Enhancements for Open networks
For many years, open networks have given security professionals heartburn because there has been no mechanism for encrypting data over the air between the endpoint and the AP. In the early days, this was significant since Internet traffic and even most internal applications didn’t use encrypted protocols — meaning, if a user was connected to an open network, most or all their data was easily sniffed through passive eavesdropping and could be read in plain text without any special tools or password cracking.
While the vast majority of Internet traffic is encrypted now, it still only takes one poorly designed site or application to put a user (and an organization) at risk. Password reuse is not just common, it’s still rampant. If you’re curious about the uptake of HTTPS across the Internet, Google reports it saw a steep 50% increase from 2014 to 2020 and has stayed steadily around the 95% mark since.
I think most of us can agree with an entire suite of cryptographic protocols at our disposal, it’s just negligent to not encrypt over-the-air communication within any business network.
Enhanced Open
And hence Enhanced Open was born. You see, when an Open network and Encryption love each other very much….
To solve the problem of unencrypted traffic, the Wi-Fi Alliance created a program for Enhanced Open. Announced in 2018, most enterprise Wi-Fi vendors began supporting the feature in mid to late 2021. Enhanced Open adds encryption to open authentication networks, offering protection from passive eavesdropping.
Based on Opportunistic Wireless Encryption (OWE, RFC 8110) the feature uses an anonymous Diffie-Hellman exchange to securely negotiate encryption keys without requiring user or device authentication. Like the WPA3 suite of security, Enhanced Open also requires PMF to add integrity and confidentiality to Enhanced Open networks.
Migrating from Open to Enhanced Open
Before I get into the Transition Mode options for Enhanced Open networks, let me be transparent in saying this feature is not yet supported by all endpoints (in fact as of today, Apple doesn’t support it). Also, perhaps more of an issue for us as architects is that the WiFi system manufacturers all handle Enhanced Open configuration differently. In short, it can be messy and unpredictable but that will change as the technology matures. I had a heck of a time trying to get Enhanced Open (OWE) screenshots and packet captures for the book.
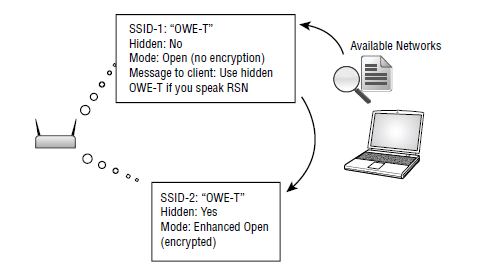
The Enhanced Open Transition Mode works very differently than Transition Mode in WPA3-Personal and WPA3-Enterprise. TL:DR It will broadcast one Open SSID, and then point capable endpoints to a hidden Enhanced Open SSID, usually with the same name. As you might imagine, that can confuse certain older and less capable endpoints so mileage will vary, your experience will change over time, and please test and retest before you roll it out.
Unlike the security concerns I have in the other Transition Modes, most Open networks are used for Internet-only and guest portals which means there’s usually little to no risk in using the Enhanced Open Transition Mode (as long as the endpoints support it). If it’s supported, it will be transparent to the user.
Also, while Enhanced Open SSIDs bring PMF into the picture, the exchanges used for encryption do not protect against on-path (man-in-the-middle) attacks.
Finding Security Settings in WiFi Products
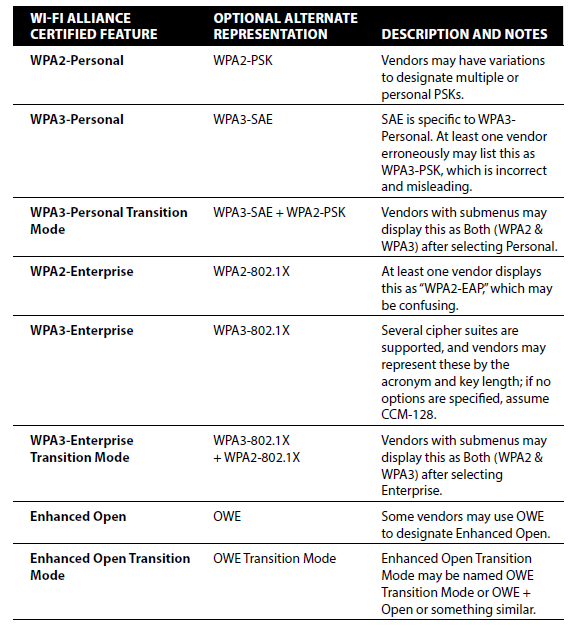
In the recent post “WiFi Security: The 3 Types of WiFi Networks” I included a sidebar on the weird naming conventions you may come across in different products. As a quick recap, the terms “WPA3-Personal”, “WPA3-Enterprise”, and “Enhanced Open” are all reserved for use by the Wi-Fi Alliance for products that have been tested and certified against those standards.
Because of that, different products and even different generations of products may show these SSID security options differently. It can be dizzying, even for a full-time WiFi professional, and nearly impossible for anyone else to decipher without a lot of work.
Here’s a current cheat-sheet pulled from the book to help you on your journey. The previous post also includes keywords and phrases you can use to identify the three different classes of networks.
Following Along with WPA3 Enhancements
Since WPA3 is planned for continuous improvement as the security landscape changes, please also visit the Wi-Fi Alliance site at https://www.wi-fi.org/security for the most up-to-date documentation on security considerations for WPA configurations.
Summary
I know this post isn’t exactly bite-sized, but I hope this is a helpful introduction to the main differences between WPA2 and WPA3, and when and how to begin considering a transition.
- WPA3-Personal is a huge security improvement over WPA2-Personal, upgrade immediately where possible
- WPA3-Enterprise brings security features that are valuable including PMF, and migrating should be very easy, especially for corporate-managed endpoints because they’ll likely not require any ‘touch’ if the drivers have been updated
- Only use Transition Modes for Personal and Enterprise when needed, and only for the length of time required; don’t enable Transition Mode and walk away, you’ll need to touch some endpoints along the way
- Enhanced Open adds encryption to Open networks but is a bit messy at the moment
- Naming conventions for security options and Transition Modes will vary by product based on which are certified with the Wi-Fi Alliance and will change over time
What’s next? Now that you’ve gotten a nibble of WPA3, coming up next is a more detailed migration guide and recommendations getting from WPA2 to WPA3 with varying degrees of flexibility versus security.
Cover photo credit photo by Dreamlike Street on Unsplash.








[…] Security Uncorked. Wi-Fi security: WPA2 vs. WPA3 – security uncorked. (n.d.). Retrieved February 16, 2023, from Securityuncorked.com website: https://securityuncorked.com/2022/08/wifi-security-wpa2-vs-wpa3/ […]
Hi,
Thanks for the article.
Do you know if WPA3+PMF would cause client performance issues? Since it’s introducing encryption by the software?
Hi Jake!
Most of the PMF features are for integrity by way of verifying authenticity through identity, versus encryption of the packets. For the parts that are encrypted, it would be low overhead. Network security use cases rely on asymmetric encryption (e.g., PKI/public/private pairs) to exchange keys and then switch to a very fast and efficient symmetric algorithm. Elliptic Curve Cryptography (ECC) is also becoming a mainstay of many WiFi uses and that’s an even lighter processing overhead.
[…] Previous WiFi Security: WPA2 vs. WPA3 Next Wireless Segmentation and Filtering Deep Dive […]