Segmentation plays a critical role in securing networks, including and especially wireless networks. Whether we’re talking about standard 802.11 WLANs, private cellular/CBRS, or IoT-based sensor networks, there will be some need for segmentation to divide the environment into logical segments, and/or to control or filter traffic between the wireless and wired environments.
Why and When to Segment Traffic
Traffic is segmented in different ways and for different purposes such as to:
- Secure management and control access from end users
- Separate different classes of networks, defined by sensitivity or asset value
- Isolate and protect legacy endpoints that present security risk
- Prevent disruption from large network broadcast domains
- Protect network segments in scope for compliance requirements (such as PCI DSS)
Methods to Enforce Segmentation
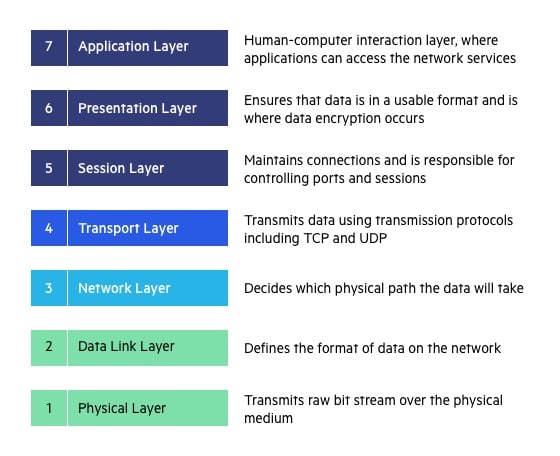
Segmentation can happen in many ways and at many layers of the Open Systems Interconnection (OSI) network stack, from the physical layer (layer 1) up through application layer (layer 7) with “micro” segmentation technologies, and everywhere in between with virtual LANs (VLANs) and access control lists (ACLs) at layers 2 and 3, respectively. And, if you can’t segment in one place, your architecture will reveal that gap and help identify another place to do it.
For example, most enterprise wireless vendors offer a feature like firewall or ACLs through policies or roles on the wireless system. With that, you could certainly implement segmentation to keep, for example, guest users from accessing the internal network. Depending on the network architecture, you could also enforce segmentation through non-routable VLANs, or routed networks with ACLs in place, or even internal firewalls.
Almost every compliance requirement and cybersecurity framework will reference and mandate segmentation in one way or another. While it doesn’t prescribe how you do it, it will outline the requirements for when to segment,
and to what degree.
To recap, segmentation methods most relevant to wireless architecture include:
- Layer 1 physical segmentation (air gap)
- Layer 2 segmentation through non-routable VLANs (on wired infrastructure) or inter-station blocking and other methods (over the air)
- Layer 3–4 segmentation with ACLs (this can be applied on the wired or wireless network segment)
- Layer 3–7 segmentation with software-defined networking or virtualized networking (SDN, VXLAN, IPSec, SSL) (again this can be on wired or wireless segment)
- Layer 7 and network-based microsegmentation in zero trust architectures
the IP layer, from “Wireless Security Architecture”
Factors Influencing Segmentation Methods
There are myriad factors that determine the best place (wired or wireless) to implement segmentation, and they type of segmentation used (what layer or degree of granularity), including:
- Compliance and regulatory requirements
- Network topology and distribution of users/endpoints
- Authentication or security mode (e.g., passphrase versus 802.1X)
- Data path modes of endpoint traffic (e.g., tunneled or bridged to wired network)
I’ll dive more into the filtering and segmentation details in a future post. I hope this provides a good overview of why, when, and how we segment wireless networks. Of course, most of these mechanisms and concepts translate to wired networks as well.
 | This post includes excerpts from Chapter 1 of WIRELESS SECURITY ARCHITECTURE. JOHN WILEY & SONS. More on network segmentation can be found in Chapter 2’s section titled “Understanding Data Paths” and Chapter 6 on “Hardening the Wireless Infrastructure”. |
Article feature photo of oranges by Kelsey Weinkauf on Unsplash








[…] Previous Wireless Segmentation Concepts: When, Why, and How White Papers & Guides, […]
Awesome teaser, JJ, and congrats on the book! I’ve been out of the infosec loop for a bit but my trusty RSS reader brought me here. I’ll definitely have to check it out!
It’s great to ‘see’ you and hear from you!