Learn about a five-phase design methodology that will help your company plan for and create an enterprise wireless security architecture.
As part o TechTarget’s recent coverage of my latest book, “Wireless Security Architecture”, they’ve obtained permission from Wiley to share an excerpt from Chapter 5, “Planning and Design for Secure Wireless.”
Enterprise wireless networks have been undergoing a tremendous transformation. From a changing workspace due to IoT, remote work and new generations of Wi-Fi to a multitude of sophisticated threats, the spotlight is on enterprise wireless network security. Knowing how to configure and maintain the wireless security architecture is critical to keep attackers at bay.
In Wireless Security Architecture: Designing and Maintaining Secure Wireless for Enterprise, author and security researcher Jennifer Minella provides networking and security teams a resource to follow. She starts by explaining wireless network security techniques, processes and products before outlining how to design an architecture, as well as the components and processes teams need to set up a secure wireless network.
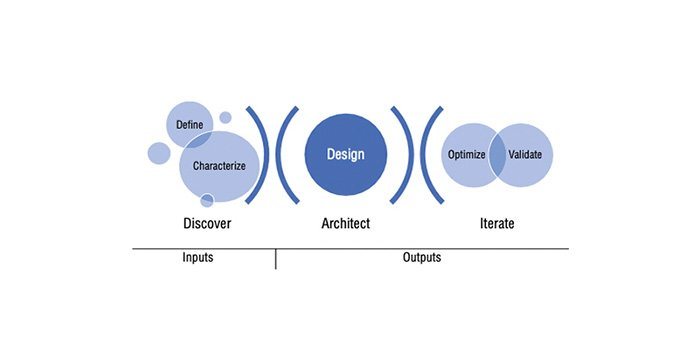
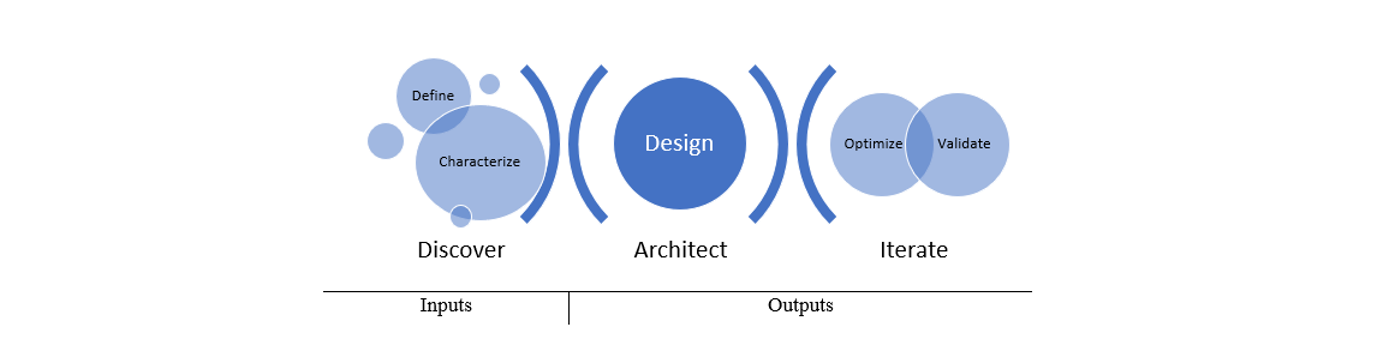
In Chapter 5, Minella laid out a guide for designing the optimal wireless security architecture. “What I’ve noticed over the years is that most networking professionals within an organization tend to wing it when it comes to planning,” she wrote in the chapter’s introduction, “often bypassing any formal scoping and documentation and skipping to configuring products.”
The excerpt introduces readers to Minella’s design methodology that follows five phases: define, characterize, design, optimize and validate.
Check out a Q&A with the author on zero trust and wireless security, UX considerations without affecting security and more.